Implement Secure Configurations | Apparel for Cybersecurity Warriors
Unisex Hoodie
Step up your cybersecurity game with the Implement Secure Configurations Hoodie. This isn’t just a hoodie; it’s a badge of honor for those who know that the backbone of digital defense lies in rock-solid configurations. Adorned with a masterfully detailed heraldic emblem that fuses medieval style with modern tech wisdom, it proclaims your commitment to securing systems in style.
This hoodie features a bold emblem centered on the back: a metallic shield guarded by meticulous wings and crowned with regal scrollwork. The striking red “SECURE” text at the heart of the crest sends a clear messagesecurity is non-negotiable. Perfect for infosec pros and tech aficionados who want their gear to speak volumes.
Product Description:
Enjoy unparalleled comfort with this unisex heavy blend hoodie. Crafted from a thick cotton-polyester mix, it offers warmth and softness ideal for long coding sessions or casual meetups. Complete with a roomy front pocket and durable double-lined hood with matching drawstrings, this hoodie is your go-to for blending comfort with cybersecurity pride.
Product Features:
- 50% cotton, 50% polyester fabric blend: Crafted for cozy warmth and durability.
- Medium-heavyweight material (8.0 oz/yd²): Ready for brisk walks through threat landscapes or chilly offices.
- Classic relaxed fit: Allows ease of movement and layering.
- Tear away label: For irritation-free wear during marathon hacking sessions.
- Double-lined hood with color-matched drawcord: Built tough for style and function.
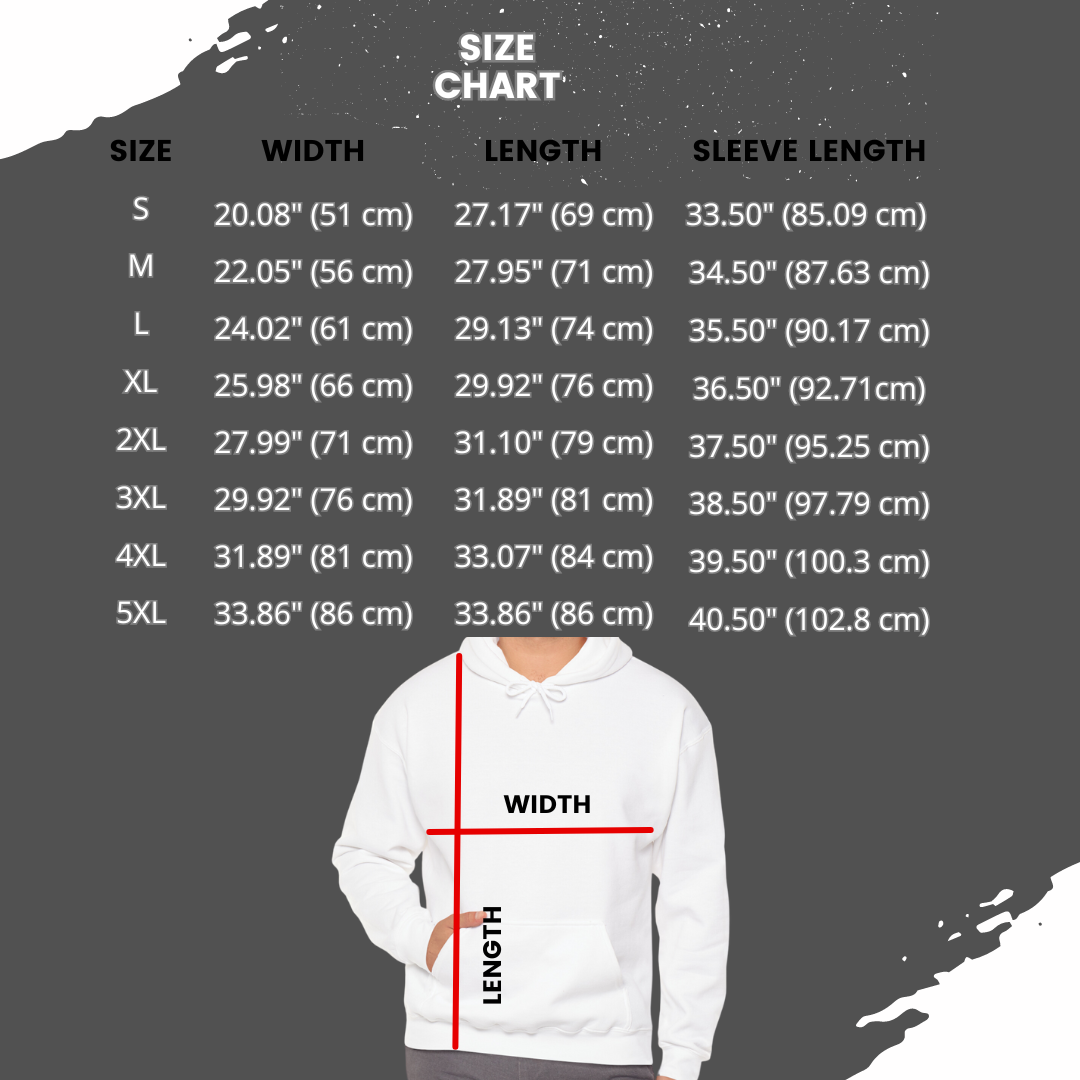
- Runs true to size: Find your perfect fit without guesswork.
Embrace the art of implementing secure configurations with apparel that champions your expertise and style. This hoodie is your armor for both the digital battlefield and everyday life.